As we progress and evolve in the online landscape, most of us like to think we would cotton on to a phishing attack pretty quickly. Unfortunately, would-be hackers are also learning to progress and evolve their attempts at worming their way past your network defences and infiltrating your systems.
Phishing attacks typically come in the form of a message (usually email) designed to lure you into clicking on a link to a dodgy website or willingly handing over your personal information at their urgent request.
Most of these messages have gotten more convincing over time as compared to a decade ago when a prince from another continent said you were their only living relative and wanted you to inherit a lazy 15 million – all you had to do was give them your details and pay the transfer fees.
Here are some very obvious ways to tell if emails are phishing scams:
Take a look at the sender’s details
Doing something as simple as closely inspecting the sender’s email address could save you a world of hurt. If you hover your cursor over the sender’s name, it will display their full email address. Pay particular attention to misspelt words, stray hyphens, or unfamiliar domain names. For example, the sender might be ‘Bob McTrustworthy’, but his email address is actually ‘d110_2rfdaad@hax.host’. Another, less obvious differentiation between legitimate senders and phishers might be something like info@paypal.com versus acounts.user@pay-pal.com. If you have any prior communications or contact details for the alleged sender, it’s a good idea to put them next to each other and see if they match up.
The message is asking you to do something urgently
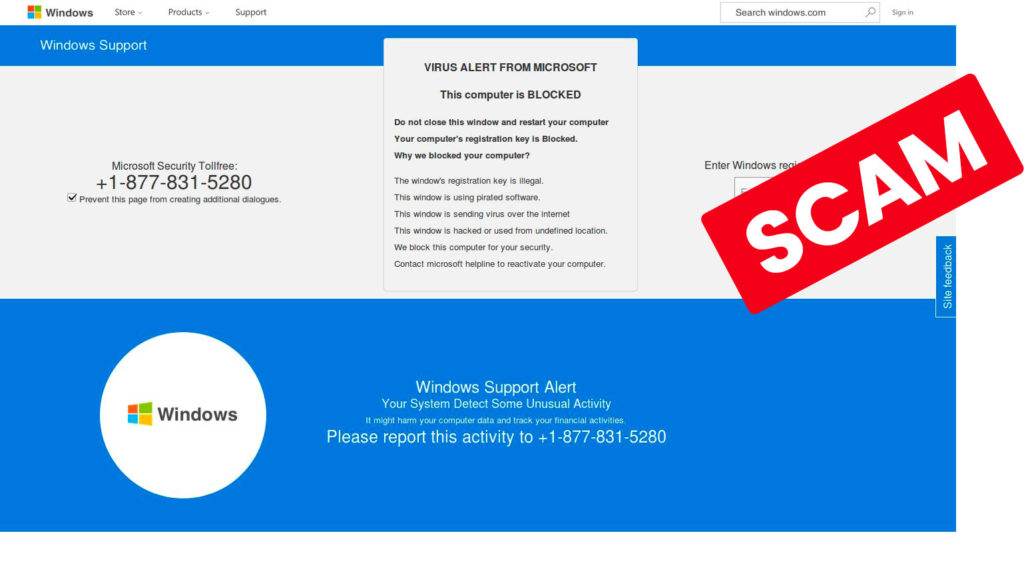
“Your computer has a serious infection! You must IMMEDIATELY click this link to scan and remove all viruses.”
“Your account information has been hacked. Click here to log on and change your password URGENTLY.”
These are both examples of phishing scams designed to spark fear and a sense of urgency into recipients to fix a serious problem that doesn’t exist. Regardless of how legitimate the message may seem; it always pays to be cautious and take time to inspect the URL of the link they’re suggesting you should click. You can do this by hovering your cursor over the link and determining whether the address is secure with ‘https://’ at the beginning and actually goes where it says it’s going. Phishing scams typically direct you to dodgy links and websites that have sinister URLs.
There are no signatures, icons, or official branding
Legitimate senders will usually use HTML formats and list their contact details at the bottom of an email in the form of an email signature or some kind of official logo, banner, or other imagery that act as a hyperlink to their website or social media. Phishers can be pretty lazy and simply use plain text emails to convey their messages. Sometimes, they also do the polar opposite and use a hyperlink image of text as a call-to-action to click on and direct you to a sketchy website. If you can’t see any shred of evidence that the sender is from where they say they’re from, it’s best not to click on any links at all.
Phishing attacks aren’t always obvious, and your team may not all have the same level of caution which can leave the security door wide open for hackers. The best way to control the risk is to eliminate it altogether with effective blocking mechanisms to stop them dead in their tracks before they even get a chance to land in your inbox.
Chat to us today about how we can help you stay protected from phishing scams.


